Tor is one of the easiest ways to browse the web anonymously. But now that we’ve said the “a” word, we need to put a big ol’ asterisk next to it, because using Tor to conceal your online activities comes with a bunch of caveats. Let’s take a look at what Tor does, who uses it, and most importantly, what Tor won’t do if you’re looking to hide online.
If you’re new to internet privacy and security, you’ve still probably already read references to something called Tor — a widely hailed piece of internet-connected software with its own internet browser. Tor is embraced by privacy aficionados for its reliable encryption and its history of covering users’ internet tracks.

At first glance, the terminology around Tor can seem intimidating and alien. Don’t worry, though. It’s simpler than it seems.
What is Tor?
Back in the mid-’90s, when the US Navy was looking into ways to securely communicate sensitive intelligence information, a mathematician and two computer scientists emerged from the Naval Research Lab with something called “onion routing.” It was a new kind of technology that would protect your internet traffic with layers of privacy. By 2003, The Onion Routing project, acronymed Tor, was in the hands of the public, where its vast network of users — the engine enabling Tor — has since continued to grow.
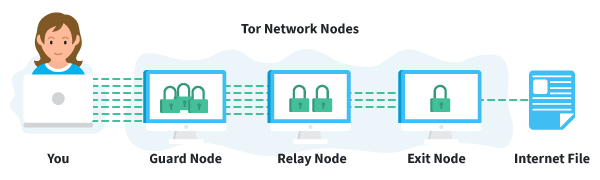
Today, thousands of volunteers all over the world are connecting their computers to the internet to create the Tor network by becoming “nodes” or “relays” for your internet traffic.
At a basic level, Tor is a type of internet-connected network with its own internet browser. Once you connect to the internet with the Tor browser, your internet traffic is stripped of its first layer of identifying information as it enters the Tor network, and is then sent bouncing through those relay nodes, which serve to encrypt and privatize your data, layer by layer — like an onion. Finally, your traffic hits an exit node and leaves the Tor network for the open web.
Once you’re in the Tor network, it’s nearly impossible for others to track your traffic’s manic pinballing path across the globe. And once you leave the Tor network via an exit node, the website you view (assuming it has HTTPS in front of its address) isn’t sure which part of the world you’re hailing from, offering you more privacy and protection.
How do I use Tor?
Normal web browsing is easy with Tor. Head to the official site and download the Tor browser. Follow the installation instructions as you would with any other program. When you open Tor for the first time, the program will ask you to either configure your connection (if you’re in a country where Tor has been banned, like China or Saudi Arabia) or simply connect. Once you click connect, Tor may take a few minutes to find a set of relays to connect you through.
But once you’re in, you can use Tor just as you would any other browser. You’ll also be prompted to review your Tor browser security settings. If you’re aiming for maximum privacy, I’d advise leaving the settings on their default selections.
If you start experiencing slower-than-normal speeds, you can nudge Tor into action by checking for a quicker connection path to the website you’re trying to view. In the top right corner of the Tor browser, click the three-line menu icon and select New Tor Circuit for this Site.
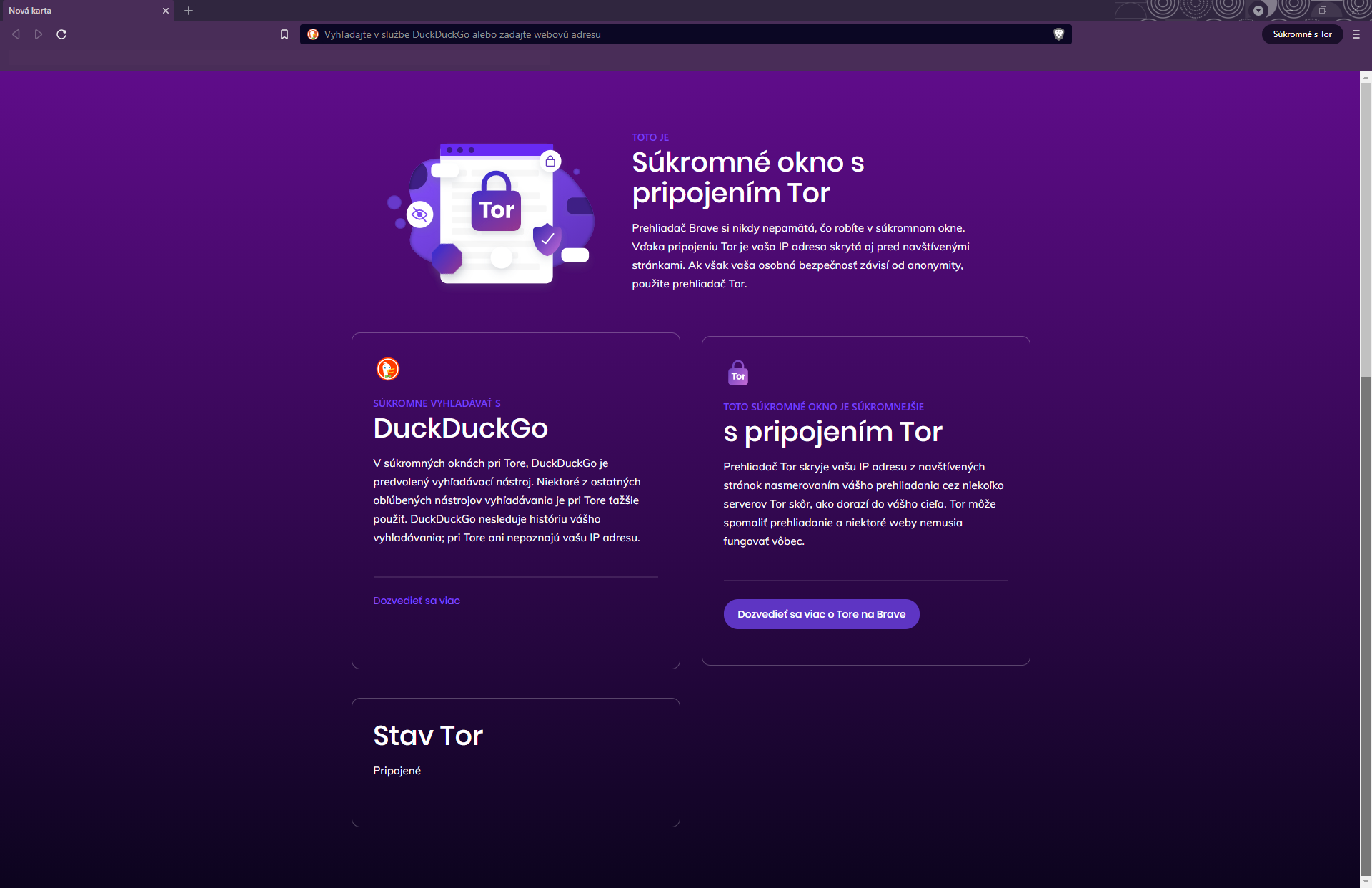
The privacy-focused Brave browser also has an option to route traffic through Tor when inside a private window.
How to download Tor browser
All you have to do to access Tor is download the Tor browser. Launch it, and everything you do in the browser will go through the Tor network. Most people won’t need to adjust any settings; it just works. That said, since your data is going to hop through a lot of relays, your experience on Tor might be more sluggish than your normal internet browsing.
 Simply click on the Download button
Simply click on the Download button
 Choose a platform for which you would like to use Tor browser
Choose a platform for which you would like to use Tor browser
How to Run Tor browser
After your download is finished, open the downloaded file and follow that simple installation wizard to complete setup.
Once your installation is done, you can now open the Tor browser for the first time.
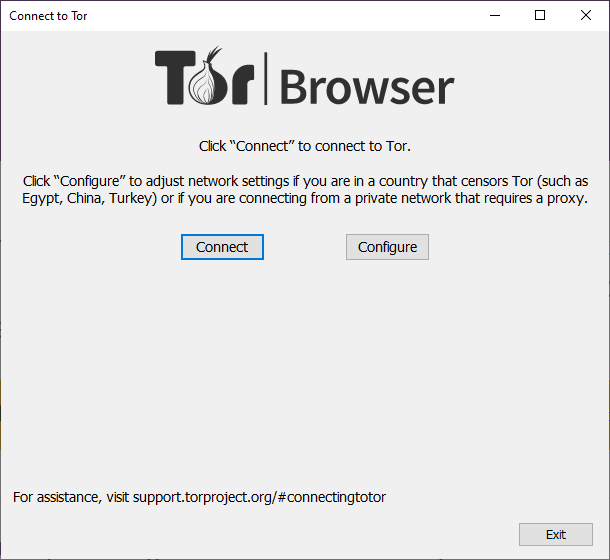
Before we finally open the Tor, you can change your setting based on you situation accordingly when you hit the ‘’Configure’’ button.
If everything is set, you can now click on the ‘’Connect’’ button. You will get a loading screen with the status bar of establishing a circuit.
And after this loading screen, you will finally get to see this view:
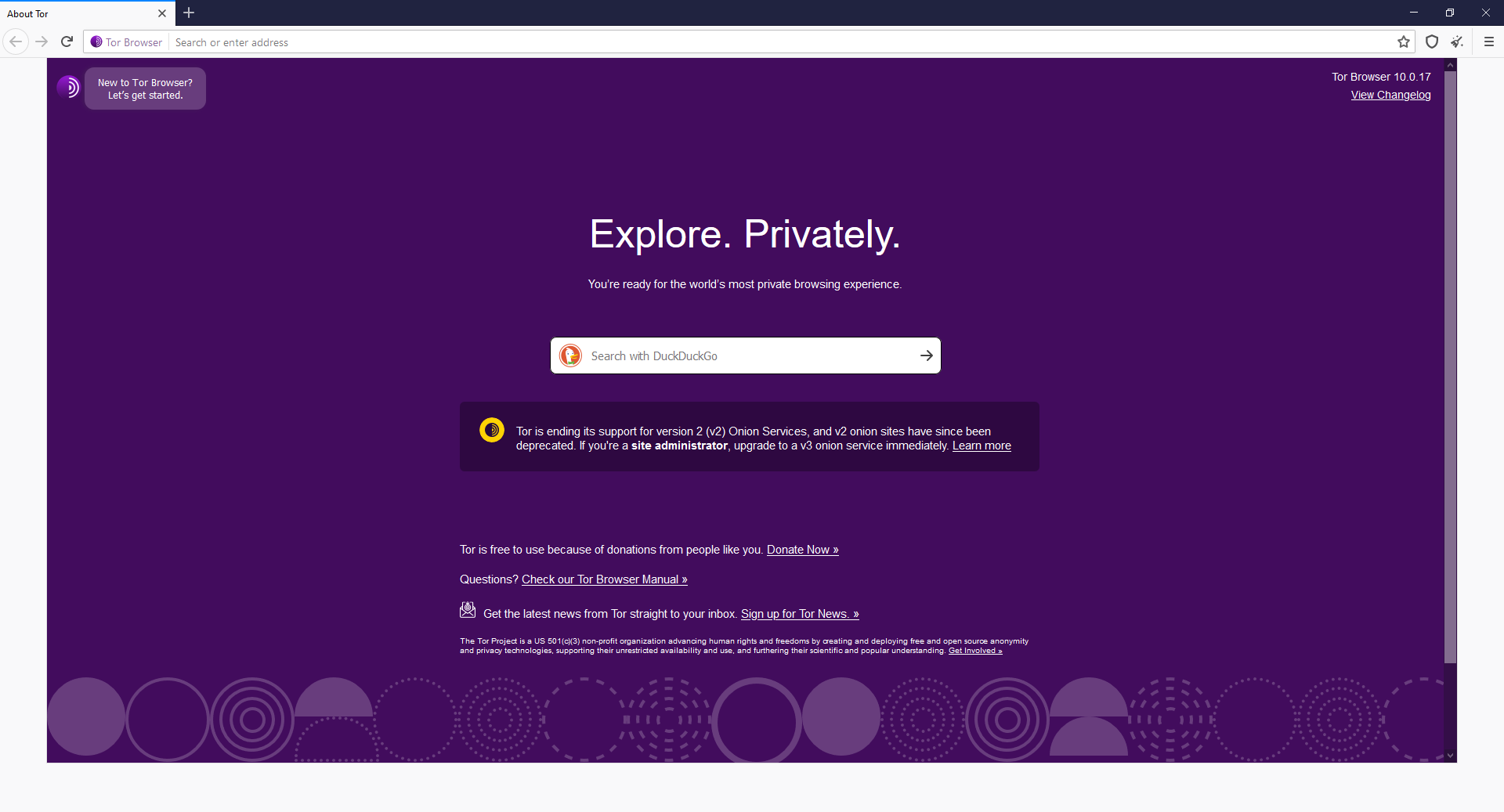 Tor homepage
Tor homepage
As you can see, the search engine is set to Duckduckgo.com instead of google. This change itself will already result into different search results. What is more important, you are now connect via tor circuit and your connection is now much more secure.
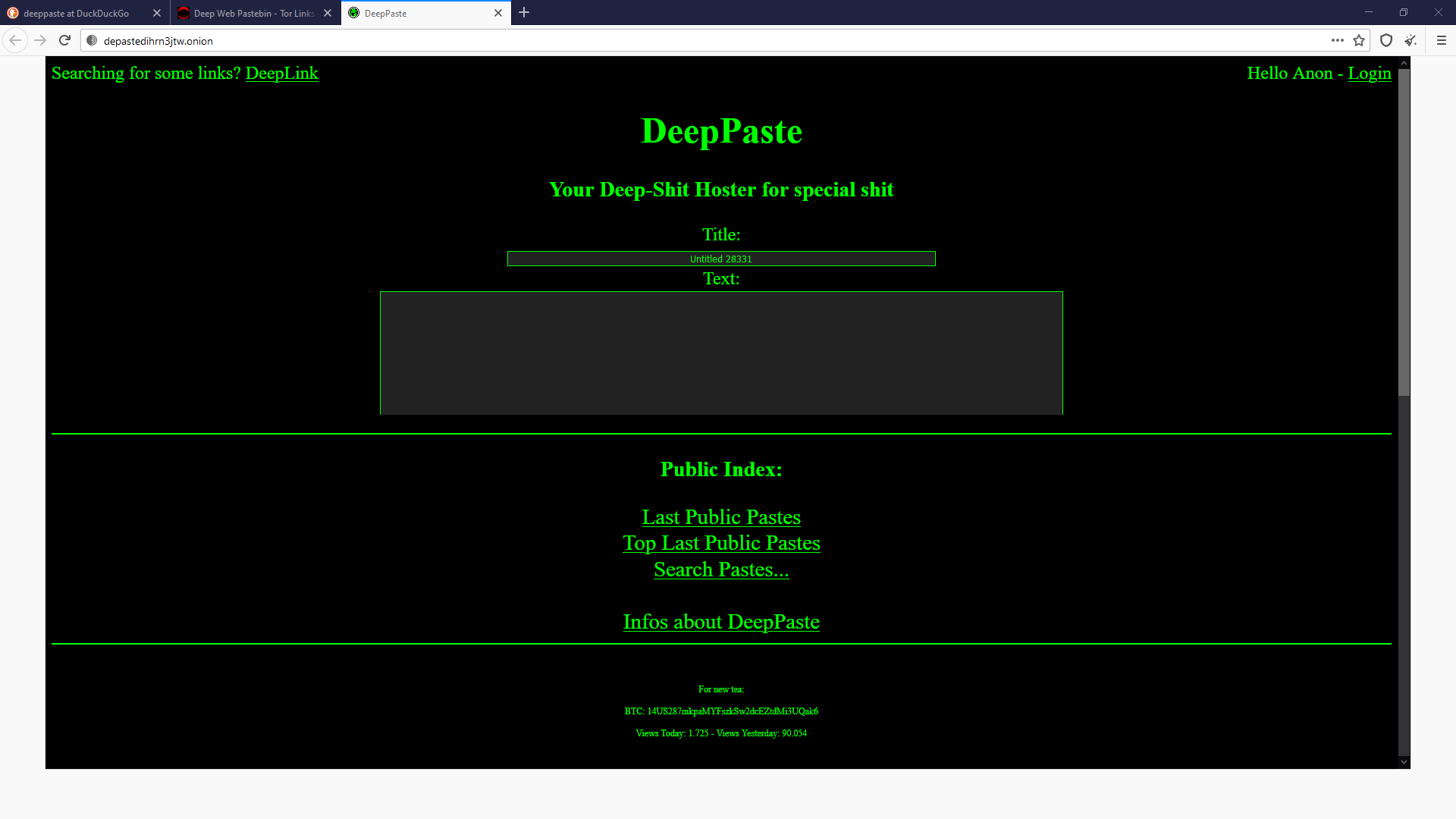
But that’s not everything. You can now visit the ‘’onion’’ sites. An example of URL address on dark web is as following: http://depastedihrn3jtw.onion/, web site that serves as a simple ‘’market’’ with services, people post here any information and it’s up to you what you will search for on this website.
This website in particular is just one of the millions websites you can now access. You are now able to access next level of iceberg. Not only to visit unindexed websites in deep web, but all that interesting information from dark web as well.
To have some fun yourself and to see what is possible to find here, what kind of information you can access, you can start with browsing link on Hidden Wiki – there are multiple categories from search engines, markets, blogs, porn, hacking to communication. You will find everything, so be ready!
A preview of what a private Tor window looks like in Brave:
When it comes to anonymity on the internet, you need to be careful when browsing any site, especially if it is the dark web. For maximum anonymity, it is therefore advisable to use an anonymous device on which you have set up a Virtual Workstation – such as VMware – running the Linux operating system. In this Virtual Space, we recommend using a good quality paid VPN service before connecting using Tor.
Are there any downsides to using Tor?
Because Tor is a volunteer-run network, speed can often be an issue. As your traffic moves from node to node, you’re likely to notice more speed loss than you would, for instance, with most commercial virtual private networks. This becomes particularly noticeable if you try to watch streaming Netflix content over Tor or make voice-over-IP phone calls or video calls with an app like Zoom. Tor technology isn’t necessarily built to provide seamless audio-video experiences.
Speaking of videos, there are also limits to the amount of privacy Tor can offer you if you enable certain browser media plugins like Flash. Likewise, your browser’s JavaScript plug-in — which enables you to view a lot of websites’ embedded media — can still leak your IP address information. Torrenting files with Tor also exposes you to privacy risks. Because of these risks, Tor’s privacy settings have these kinds of plug-ins disabled by default.
If you’re just looking to do general, daily internet perusal using a browser that will better hide your traffic from spying eyes, Tor probably isn’t the best choice due to its slow speeds and incompatibility with most embedded media. But if you’re concerned enough about privacy around a particular topic of internet research (and you don’t have a VPN), Tor is probably the best choice for you.
Is Tor Legal?
The use of Tor itself is completely legal in most jurisdictions, especially in the “western world”. However, as we mentioned, some people use it for illegal activities, because of the anonymity the software helps users achieve. Using Tor doesn’t make these activities any less illegal. Therefore, we want to strongly advise you to refrain from such practices.
Will Tor work with a VPN?
In some cases, yes. Most of the time, however, it takes some know-how to be able to configure your VPN’s connection to work in harmony with Tor. If you don’t get it right, you can risk making both Tor and your VPN ineffective when it comes to protecting your privacy. We recommend getting familiar with both types of software before marrying the two.
On the plus side, however, a successful combination of the two can be useful. While Tor protects your internet traffic, your VPN can be set to encrypt the internet traffic of any other applications running on your device in the background.
To investigate VPNs further, check out our beginner-friendly guide to all the VPN terms you need to know and our directory of the best VPNs.
Tor Over VPN, or Vice Versa?
There is always the debate about which tool is better, VPN or Tor; and for a short answer: it depends.
However, I want to talk about increasing anonymity over the Internet and improving security of web traffic by using a combination of these tools. There are benefits and drawbacks of doing so, and the order makes a difference.
Tor for Anonymity
Tor has always been considered providing stronger anonymity than VPN; your data first arrives at the network through a random node around the world. It then makes a minimum of two hops, eventually passing through a random exit node to its last destination — no sole node will see the whole picture of your activities:
· The entry node will see your location, but not who you are communicating with.
· The exit node will see who you are communicating with, but not your location.
You are anonymous, but your activities are not 100% private.
VPN for Privacy
VPN, or Virtual Private Network, encrypts internet traffic, usually only routing through one hop. They retain stability and speeds, faster than Tor, to paying consumers. The benefit of using a VPN is that your ISP is not privy to your internet browsing habits, and network traffic.
You are not anonymous, but your activities are 100% private — apart from the VPNs that keep user logs and are cooperative with law enforcement.
Using TOR over VPN
User → VPN → Tor → Internet
To use this setup, you need to connect to your chosen VPN server, and then launch the Tor Browser. The VPN encrypted traffic would transmit to the Tor network via a couple Tor hops prior to reaching its destination. Benefiting from Tor’s anonymity and a VPN’s end-to-end encryption makes is a powerful combination for safe internet browsing.
Pros:
- Easy to setup
- Fast and stable
- VPN provider cannot see your traffic content or origin — only that you have connected to the Tor node.
- ISP cannot see that you are using Tor, only that you are using a VPN.
- Tor entry node will see your VPN IP address and not your real IP address.· Hidden Tor sites are still accessible.
Cons:
- VPN provider can still see your real IP address and provide that info to law enforcement (LE) if they are LE friendly.
- If you are sending unencrypted traffic, you are vulnerable to malicious Tor exit nodes.
- If your VPN suddenly drops, your activities risk to be exposed to your ISP.
- Without using a type of end-to-end encryption, you are placing all your trust into the exit node operator.
Using VPN Over TOR
User → Tor →VPN →Internet
To use this setup, you connect to the Tor Browser first, and then launch your VPN; your traffic becomes encrypted after being connected to the Tor nodes.
Pros:
- Increased privacy from the VPN providers as they cannot see your real IP address.
- Your ISP can’t see that you are using a VPN, only that you are using Tor
- Ideal for anonymous purchasing via Bitcoin
Cons:
- Very slow in performance
- You can only access hidden websites
- Very few VPN providers allow this setup
- ISP providers do not favour Tor usage
- The Tor network does not approve of this setup since they believe that the VPN server can establish a profile of all of your activities and that over time that can be extremely detrimental to the user.
- Very susceptible to end-to-end timing attacks which are employed to deanonymize VPN and Tor users by associating the times they were connected to such anonymity services
Conclusion
When using the combination of the two tools, it becomes exceedingly difficult to identify you. At the end of the day, the option is up to you depending on what you wish to accomplish via your internet browsing and activities.








